Monday, July 30, 2007
For the first time - 4.1.2 CAM/CAS guides in HTML
http://cisco.com/en/US/docs/security/nac/appliance/configuration_guide/412/cam/412_cam_book.html
CAS Guide:
http://cisco.com/en/US/docs/security/nac/appliance/configuration_guide/412/cas/412_cas_book.html
Friday, July 27, 2007
NAC Version 4.1.2
Cisco NAC Appliance Software Download Page
Requires a valid Smartnet contract in order to download
4.1(2) Documentation Page
Some of the feature "enhancements" that i found interesting and useful:
- NEW Cisco NAC Network Module (NME-NAC-K9) Support
Release 4.1(2) introduces support for the Cisco NAC Appliance network module (NME-NAC-K9) on the next generation service module for the Cisco 2811, 2821, 2851, 3825, and 3845 Integrated Services Routers (ISRs).
The Cisco NAC Network Module for Integrated Services Routers supports the same software features as the Clean Access Server (CAS) on a NAC Appliance, with the exception of high availability. NME-NAC-K9 does not support failover from one module to another. The integration of CAS capabilities into a network module for ISRs allows network administrators to manage a single device in the branch office for data, voice, and security requirements. The NME-NAC-K9 network module is available as a single hardware module with 50-user and 100-user license options, and supports a maximum of 100 online, concurrent users.
Once initially installed, the Cisco NAC network module is managed in the CAM web console like any other Clean Access Server, and a single CAM can manage both CAS appliances and NAC network modules. To add the Cisco NAC network module to your network, at least one Clean Access Manager appliance (Lite, Standard or Super) must be already installed and configured.
Cisco ISR platforms need to run Cisco ISO software Release 12.4(11)T or later (IP Base image or above) in order to support the Cisco NAC network module.
If introducing the Cisco NME-NAC-K9 network module to an existing Cisco NAC Appliance network, you must upgrade all CAM/CAS appliances to release 4.1(2) for compatibility.
Look out for an upcoming blog entry to show how to deploy the Network ModuleUTILIZE THE GUI:
CAM web console:
Device Management > CCA Servers > Manage [CAS_IP] > Network > IP | new Platform field featuring either "APPLIANCE" or "NME-NAC"
CAS web console:
Administration > Network Settings > IP | new Platform field featuring either "APPLIANCE" or "NME-NAC"
The CAS CLI includes the new service perfigo platform command in release 4.1(2). The command allows you to determine whether the CAS is a standard Clean Access Server appliance or a new Cisco NME-NAC-K9 network module installed in a Cisco ISR router chassis. The command output includes either "APPLIANCE" or "NME-NAC" as the platform setting.
- Debug Log Download Enhancement
Beginning with release 4.1(2), you can now specify the number of days of collected debug logs to download in order to aid troubleshooting efforts when working with Cisco technical support. Previously, debug logs compiled to download to technical support included all recorded log entries in the CAM/CAS database. The default setting is one week (7 days).
To review all enhancement, caveats and upgrade procedures please read the following release notes:
Cisco NAC Appliance 4.1(2) Release Notes
Please note that it is best practice to follow the upgrade procedures to the "T" when upgrading your NAC Managers and Servers.
For those of you just getting into the land of NACA, there is a very good presentation on the features that came about in Release 4.1(0) located on CCO called "What's New in Cisco NAC Appliance 4.1" that should catch you up on the latest and greatest features.
Saturday, July 21, 2007
Configure and Troubleshoot the Active Directory Windows Single Sign On (SSO)
NAC Appliance (CCA): Configure and Troubleshoot the Active Directory Windows Single Sign On (SSO)
Friday, July 20, 2007
VPN Deployments with ASA 8.0
One common design challenge in the past was how to deploy NAC for VPN Users when the VPN device is also a corporate firewall. This entry will hopefully help you understand the existing ways of deploying NAC for VPN Users and also help you understand how to design NAC for VPN Users with ASA 8.X.
NAC For VPN Users with a standalone VPN Device:
This is the typical deployment for VPN Concentrators, PIX/ASA (for vpn only), and IOS VPN Routers(for vpn only). The CAS is typically and preferred to be deployed in Virtual Gateway Mode. VG allows for zero IP Address changes and only requires the addition of 1 Authentication/Untrusted VLAN. For more information on how to configure NAC for Standalone VPN Devices please see the NAC Appliance (Cisco Clean Access) In-Band Virtual Gateway for Remote Access VPN Configuration Example
Figure 1 - VPN Deployment with a Standalone VPN Device
With this deployment you need to ensure normal internet traffic from corporate users does NOT go through the CAS. In order to accomplish this, the CAS is deployed using Real-IP Gateway and policy based routing is used on the next layer 3 hop from the firewall to send VPN Users traffic to the CAS's untrusted interface.
Figure 2 - VPN Deployment with a 6.X/7.X Corporate Firwall & VPN Device without a DMZ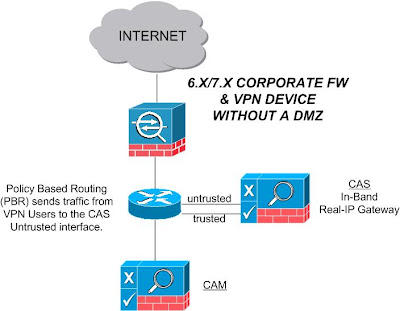
In this scenario the PIX/ASA has a DMZ interface that is hosting public servers. If we look to the same deployment option as before, it presents a problem: VPN Users are able to get to the DMZ without having to go through NAC. This leave us with a couple of options:
- Block all VPN Users from getting to the DMZ
- Only allow specific services from VPN Users to the DMZ
- Allow everything to get to the DMZ without going through NAC
- Advanced Workaround using NAT on the Core Router (Not recommended)

NAC For VPN Users with a ASA 8.X Corporate Firewall/VPN Device with a DMZ:
This is what you all have been waiting for, how does VPN Deployment change with ASA 8.0? It all comes down to one new feature "Restrict Access to VLAN" (also know as VLAN Mapping).
Restrict Access to VLAN—(Optional) Also called "VLAN mapping," this parameter specifies the egress VLAN interface for sessions to which this group policy applies. The security appliance forwards all traffic on this group to the selected VLAN. Use this attribute to assign a VLAN to the group policy to simplify access control. Assigning a value to this attribute is an alternative to using ACLs to filter traffic on a session. In addition to the default value (Unrestricted), the drop-down list shows only the VLANs that are configured on this security appliance.
This configuration option is configured within the Remote Access Group Policy:
 Please note that you must create an DOT1Q trunk and create the VPN DMZ interface using a subinterface for this option to appear. Now that we have a way to ensure VPN users get put onto a specific interface, we are able to deploy the CAS in Virtual Gateway mode and control complete access to VPN Users through NAC. This forces all users to go through NAC before they are allowed to do anything.
Please note that you must create an DOT1Q trunk and create the VPN DMZ interface using a subinterface for this option to appear. Now that we have a way to ensure VPN users get put onto a specific interface, we are able to deploy the CAS in Virtual Gateway mode and control complete access to VPN Users through NAC. This forces all users to go through NAC before they are allowed to do anything.
Summary:
Cisco's ASA 8.0 software has really made deployments with NAC for VPN Users a lot less complex. Utilizing the VLAN Mapping setting on the ASA is only going to open up doors down the road for even better seamless integration of NAC Appliance into your infrastructure.
Sources: CAS Admin Guide; ASDM Online Help
Wednesday, July 18, 2007
Cisco NAC Profiler Announcement
Great Bay Software Inc., the innovator of Endpoint Profiling for enterprise networks, today announced it has signed a worldwide OEM agreement with Cisco that adds the company's Beacon Endpoint Profiler solution to the award-winning Cisco Network Admission Control (NAC) product line. This agreement ensures that all network-attached endpoints, including non-PCs, meet the specified requirements for network access, creating the industry's most comprehensive NAC solution set.
As part of the agreement, Cisco will rebrand and sell the Beacon Endpoint Profiler as Cisco NAC Profiler. The Endpoint Profiling and Behavior Monitoring functions provided by NAC Profiler combined with the Cisco NAC Appliance solution will ease deployments and improve the security management of endpoints unassociated with specific users, such as network printers, medical imaging devices, IP phones, HVAC sensors and wireless access points. NAC Profiler can improve the return on investment for a NAC deployment by dynamically tracking the movement of these devices on the network.
The Cisco NAC Profiler provides a number of benefits both in the initial implementation of NAC and throughout the entire lifecycle of a deployment. Great Bay's Endpoint Profiling technology generates an automated inventory of all endpoints, significantly reducing the level of effort required in the implementation of NAC. The Cisco NAC Profiler informs the NAC system of critical endpoint data, including device address information, a type descriptor (printer, phone, AP, UPS, etc.), access type (a value that defines the appropriate level of access for that endpoint) and access to additional information about that device and its history in the network. This eliminates the need for manual inventories and data entry.
"We're excited to extend our collaboration with Cisco and to be part of an end-to-end NAC solution that provides a security model for all network-attached endpoints," said Steve Pettit, president of Great Bay Software. "Customers will benefit from Cisco's global business infrastructure and from the ongoing innovation this relationship will continue to deliver."
"Great Bay Software's endpoint profiling enhances an end-to-end NAC solution strategy," said Nick Chong, head of the NAC Appliance line of business for Cisco. "Cisco NAC Appliance, the leading NAC offering in the marketplace today, continues to represent the latest in technical innovation involving NAC, and adding Great Bay's profiling technology enriches our overall NAC solution."
Cisco's NAC Profiler will consist of two functional components in the NAC Appliance solution: the Profiler Server and the Collector Application. The Profiler Server will run on a dedicated appliance while the Collector Application will reside on the Cisco NAC Appliance Server. Cisco NAC Profiler is scheduled to be available in August 2007.
About Great Bay Software:
Great Bay Software Inc. is the innovator of Endpoint Profiling, a technology designed to rapidly establish and maintain a real time view of all network attached endpoints. The company's Endpoint Profiling technology has applications in enabling the deployment and administration of Network Admission Control and network-based authentication, in addressing compliance concerns related to unauthorized devices attaching to the Enterprise network, and in managing the endpoint lifecycle for all network attached devices.Summary:
I have been working with beacon for over a year now and have had nothing but success for deployments and the customers on-going operations. It is the fries with burger when it comes to NAC in an enterprise environment. Next time you are planning a NAC deployment for your integration or are sick of adding device filters every time a new phone or printer is brought up check out Beacon!
Sources: MarketWire; Great Bay Software
Sunday, July 15, 2007
Timers
Background:
Cisco NAC Appliance is a great method of threat containment by ensuring users' identity and posture, but at what point do you want to ensure that the user whom has once been compliant is still indeed compliant? This is the reason why timers are such an important aspect of any NACA Deployment. This entry will help you to understand the different options within NAC and ensure that you configure what is needed for your deployment.
The Options:
- Certified Device Timer
- Automatically Clear Certified Device List at specific intervals (X number of days)
- May clear devices based on particular CAS, User Role, Auth Provider
- May clear X amount of users at a time
- May create multiple timers to meet your needs
- Session Timer
- An Absolute Timer that is specific to the user role (X number of minutes)
- Applies to both IB & OOB
- Triggers after a preset time to kick users off the online user list
- Heartbeat Timer
- Number of minutes after which a user is logged off the network if a device is non responsive (in-band only)
- CAS sends an ARP request for the client for the set time (L2)
- CAS looks for traffic sourced from the user (L3)
- If proxy arp is enabled then the Heartbeat timer does nothing (L3)
- 5 Minute minimum
Best Practices for the use of Timers:
ALWAYS configure Certified Device Timers to enforce posture assessment after X amount of time for any Layer 2 or Layer 3 Deployment.
Use Heartbeat Timers to automatically remove inactive users when using IB.
Use User Role Session Timers for timeout of the Quarantine/Temporary User Roles and if you have a per role maximum connect time that is less than 1 day.
No matter where you are deploying NAC the discussion of how often you need to re-authenticate/posture assess a user should come up. Hopefully, you will understand the need and plan appropriately for you deployment.
For more information on how to configure these timers, please read the CAM Admin Guide or for hands on experience and instruction, please consider taking Priveon's Cisco NAC Appliance Special Operations Class.
