Background:
Many organizations require personal firewall software to be run on clients connecting into their network as a part of their security policy. This post explores how to create custom checks to enforce the use of personal firewall software on connecting clients. This is one of the most requested custom checks I receive and hopefully you will find it benefit.
Create Checks and Rules:
For this example, I am going to show how to create custom checks for 3 different types of Personal Firewall Applications. All of this software is free and can be downloaded. To create a custom check you must go to:
Device Management – Clean Access – Clean Access Agent – Rules – New Check
Windows XP Firewall Check
The most reliable way I have found to check for XP firewall is to use a Registry Check looking for the following Registry Value:
Registry Key:
HKLM\SYSTEM\ControlSet001\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile
Registry Value:
EnableFirewall
If the XP Firewall is on the Value will be = to “1”
Figure 1 – XP Firewall Check
Make sure to select the proper OS type and also “Automatically create a rule based on this check” so that you can use the rule later.
*** Please note that the registry value looked at does not distinguish between interfaces that the firewall is turned on, e.g. users could turn on the firewall for Wireless and be connected to the LAN and pass the check. If anyone finds a more reliable way, please let me know.
Zone Alarm Firewall Check
The status of Zone Alarm can be found by looking at services running on your MS OS. Zone Alarm creates service “vsmon” that can be checked using a Service Check to ensure it is running.
Figure 2 – Zone Alarm Firewall Check

Make sure to select the proper OS type and also “Automatically create a rule based on this check” so that you can use the rule later.
Comodo Firewall Check
Unlike Zone Alarm, Comodo does not create a service that we can monitor, but it does have a process running when it is turned on. When Comodo is running it runs a process called “cpf.exe”, which we can create an Application Check to ensure it is runnning
Figure 3 – Comodo Firewall Check

Make sure to select the proper OS type and also “Automatically create a rule based on this check” so that you can use the rule later.
These 3 Custom Checks should give you an idea of how to check for different type of personal firewall applications. I know this is only a list of 3 of many different SW vendors, but if you can understand how to find the information about your preferred software then you should be good to go.
Create a Requirement:
For this example I have chosen to create a Local Check to inform users that they do not have Personal Firewall Software running. Other options might be to send them to a Help-Desk website, Vendor Website or to present them with a preferred personal firewall software download. To create a new requirement go to:
Device Management – Clean Access – Clean Access Agent – Requirements – New Requirement
Figure 4 – Personal Firewall Requirement

Make sure to select the proper OS as all if you want to enforce it on all Windows OS.
Map Requirements to Rules:
Next, we must assign the rules we created from the custom checks to the new requirement. To Map Requirements-Rules go to:
Device Management – Clean Access – Clean Access Agent – Requirements - Requirement-Rules
Figure 5 – Personal Firewall Requirement-Rules Windows All
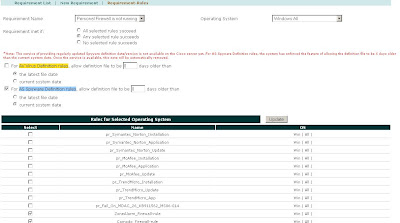
Figure 6 – Personal Firewall Requirement-Rules Windows XP

The most important notes about configuring the Requirement-Rules Mapping is to select “Any Selected Rule Succeeds” and making sure you map the rules on a per OS basis, e.g. the XP check is not applicable to Windows All, but it is applicable to Windows XP All.
Map Roles to Requirements:
Pick the role(s) that you want to enforce this requirement onto and check the new requirement. To map Roles to Requirements go to:
Device Management – Clean Access – Clean Access Agent – Role-Requirements
Then you must select the role and select the new requirement.
Summary:
Enforcement of the use of Personal Firewall Software is something that a lot of NACA deployment wants, and now you should be on the path of being able to do it.


